The all-in-one monitoring tool for your entire website
Downtime happens, certificates expire and links break.
Ensure your
website is blazing fast, error free and properly indexed without the hassle of multiple tools. Try
Oh Dear, you'll love it. These
folks already do.
-
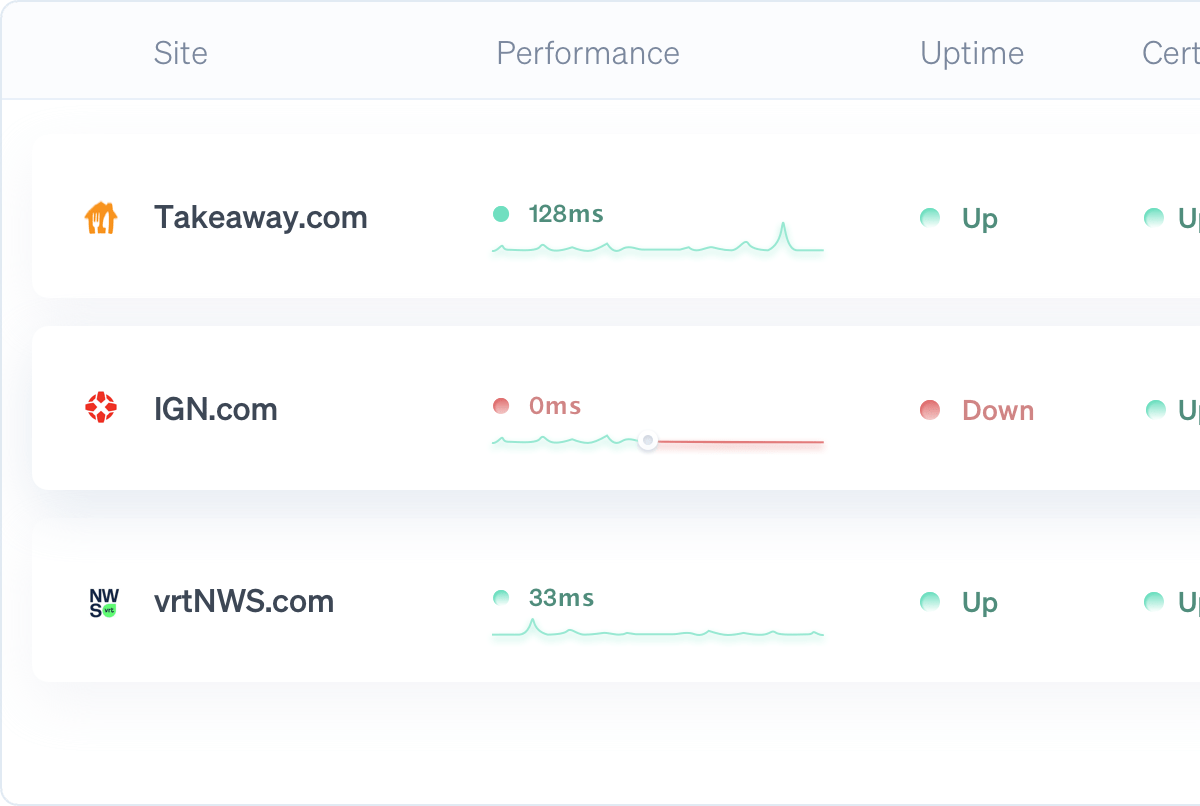
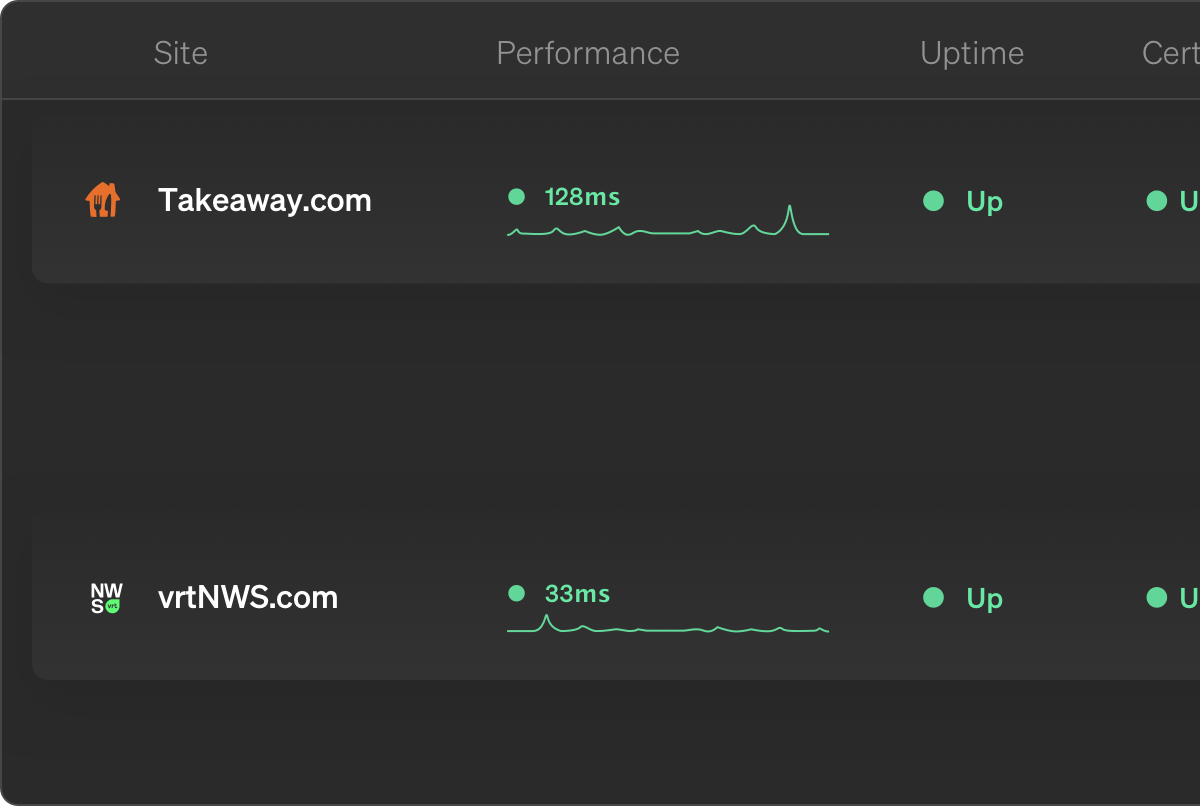
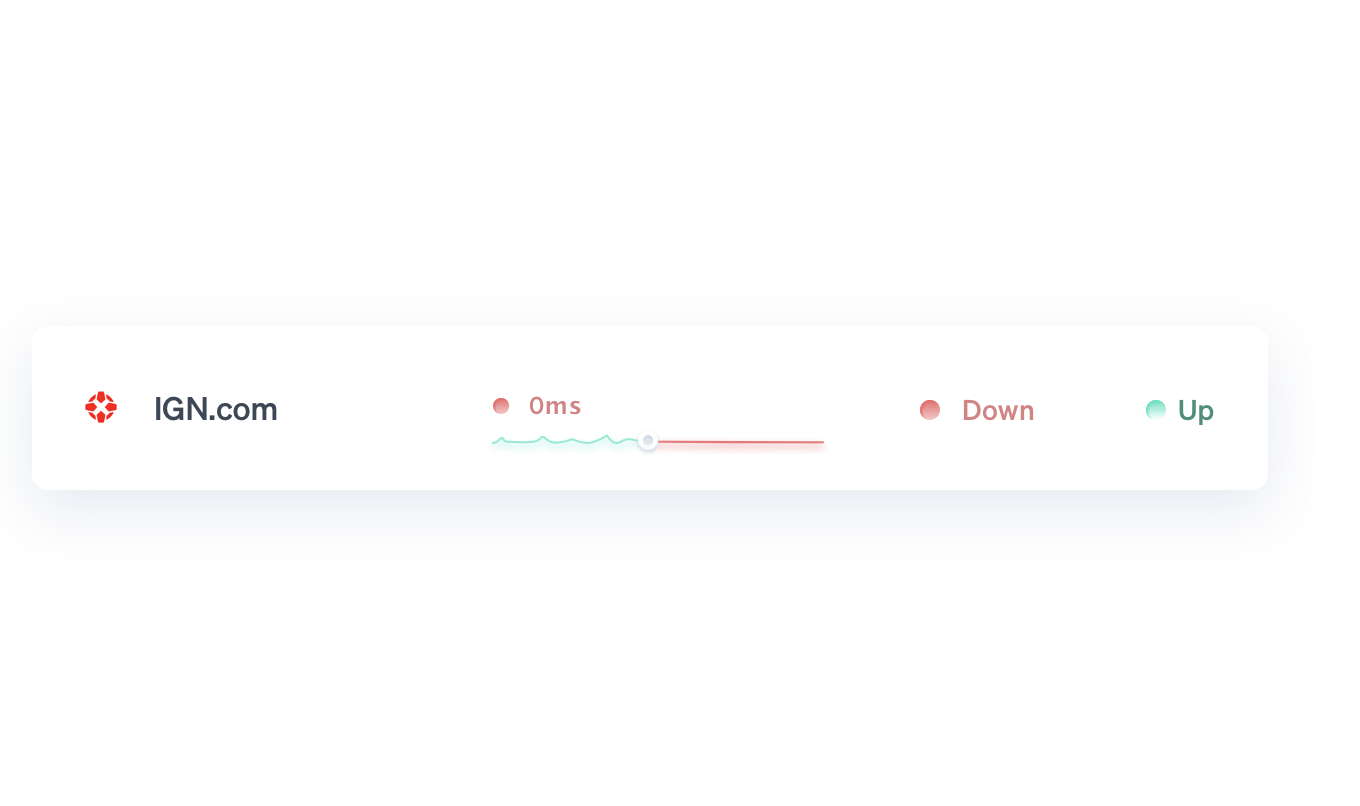
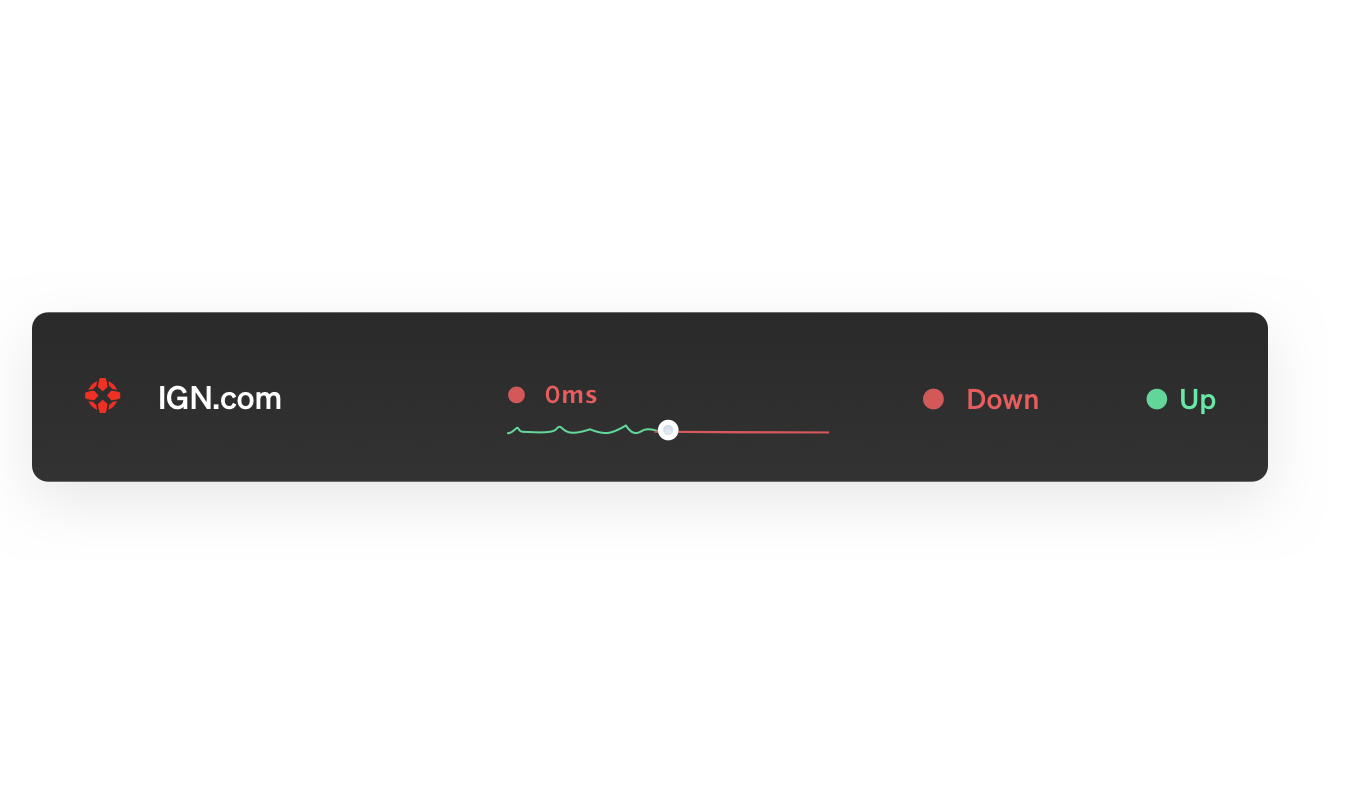
Monitor
uptime, SSL certificates, broken links, scheduled tasks and more
-
Notify
the right people when something needs fixing
-
Inform
your customers with branded status pages
Try it for free, instantly. No payment info required. Sign up if you like what you see.